In practice when it come to reproduce the exact same request, a lot of time can be spend because of a forgotten parameter or header. I often reuse the same python templates to avoid searching in the documentation as I build a new script. Seeing part of the process being repetitive, I decided to try to build a plugin for Burp.
The plugin
The plugin generate a script (in python/ruby) to reproduce a HTTP request identify in the proxy tool. It does nothing revolutionary. It only supports the first of step of building a scripted attack. It does not provide templates for specific attacks.
The scripts generated are intended to be use outside of the proxy for complete control.
Screenshots
There is not much to be said about the usage of the plugin. Here are few images that show scripts generation in both Burp Proxy and Zed Attack Proxy.
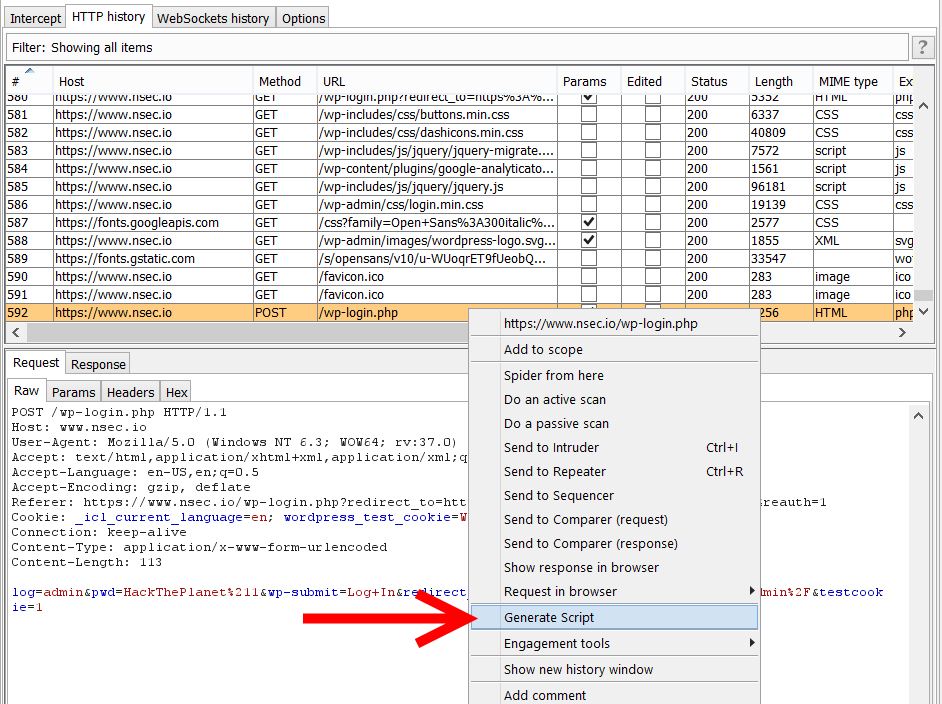 |
| Context menu in Burp Suite Pro |
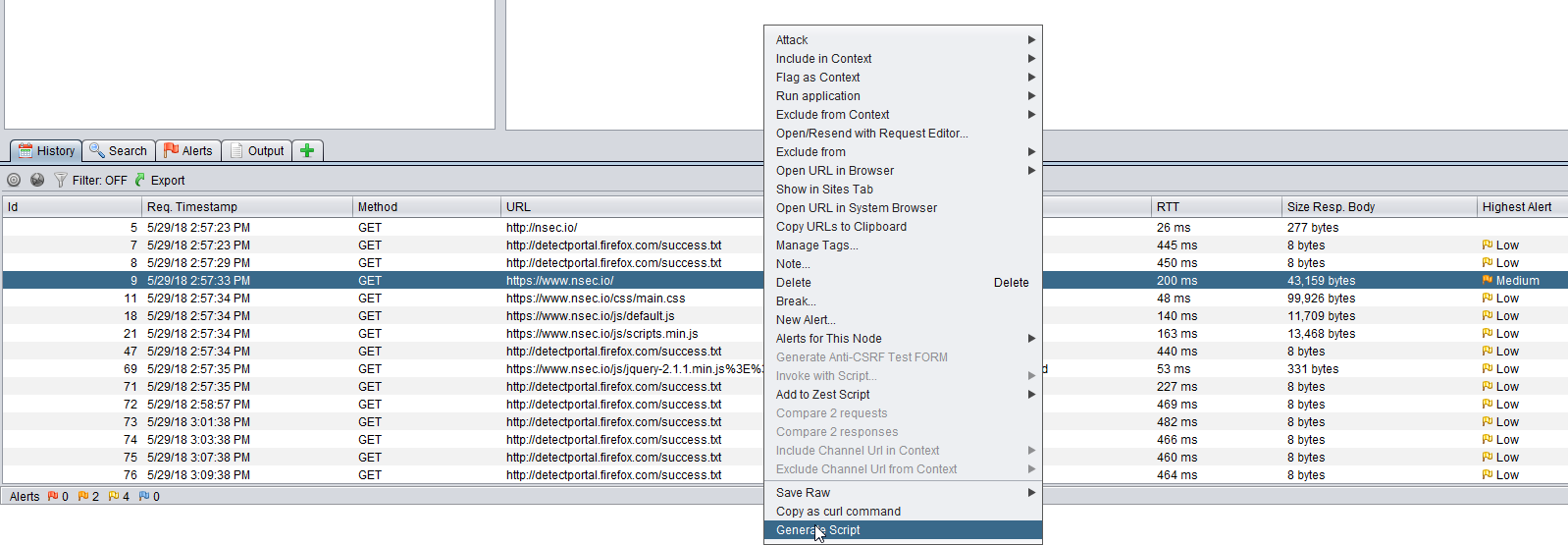 |
| Context menu in Zed Attack Proxy |
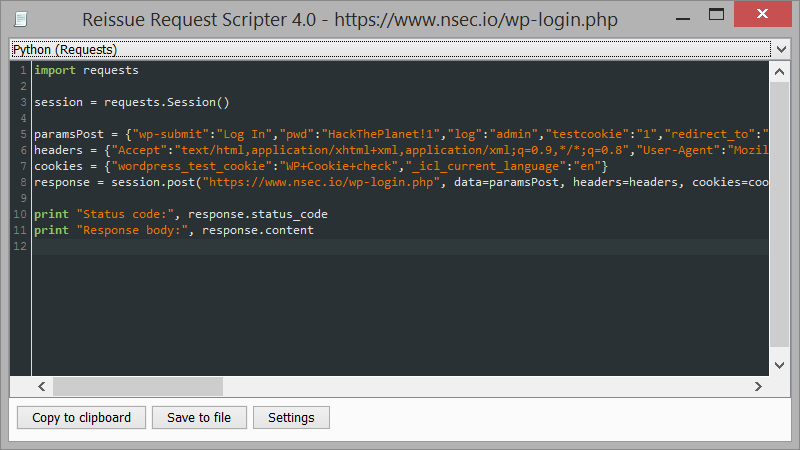 |
| Python script generated |
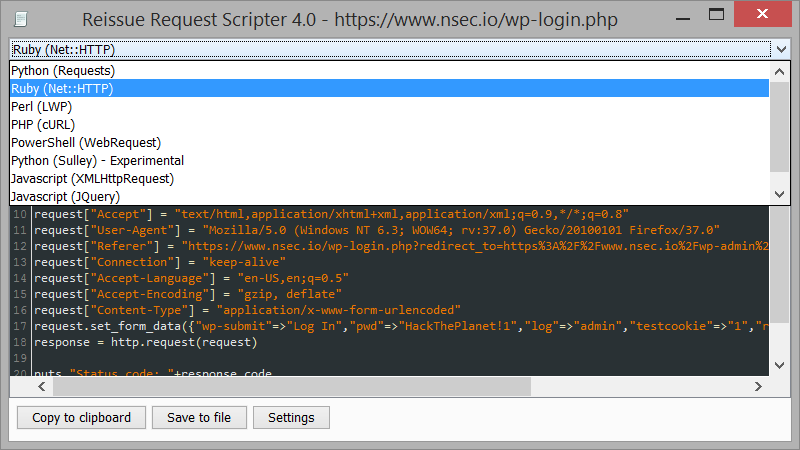 |
| Ruby/Perl/PHP languages are also supported |
Try it yourself
The Burp and ZAP plugins are available to download at https://github.com/h3xstream/http-script-generator#downloads.
Note : Burp Free edition does not supports extensions (doesn't have the Extender Tab).
Awesome tool. More usefull than Copy as curl command. A nice to have is a save option in the extension. Good work!
ReplyDeleteGreat work. A little off topic but I have solved the problem of accessing logs from Python and Ruby in a different way in IronWASP by embedding the scripting engines directly in to the tool and giving them complete access to the logs through an API.
ReplyDeleteTo pick log id 12 the code would be:
req = Request.FromProxyLog(12)
To get both the request and response:
s = Session.FromProxyLog(12)
print s.Request.Url
print s.Response..Code
You can find more details about the scripting from this blog post - http://blog.ironwasp.org/2013/10/solving-pentester-academy-web.html
Give the tool a shot if you find some time, would love to hear your feedback on its scripting support!
Cheers,
Lava
I didn't know about the tool. I will definitely try it!
DeleteA small improvement could be done: handle when the HTTP port is not standard :)
ReplyDeleteGood catch. I'll include this fix next time I do changes.
DeleteVery nice :)
ReplyDeleteWould you like this add-on to be added to the ZAP marketplace?
That way people could find and install it from within ZAP.
Have you thought about creating a new script within ZAP including the code you generate?
ZAP supports Ruby and Python with templates, and all JSR 223 compatible languages if you add the right jars to ZAP.
Simon (ZAP Project Lead)
I'm not familiar with the marketplace publishing. I have just post few questions on the mailing-list.
DeleteI don't think editing and executing scripts within the proxy is a perfect approach. It's a big goal to replace powerful editors or IDE.
I have played with the scripting engine before (Javascript). I see few interesting use-cases including searching through the proxy request/response history.
The Jython support is probably ok but again I need to stay away from my editor of choice (PyCharm) when writing scripts. Also, I don't think it is possible to divide a script in multiple files.
Fantastic plugin, thanks for making it! I have one small bug to report: for the Python script generation, a variable 'headers' is generated, but not actually used in the subsequent request. For example:
ReplyDeleteimport requests
session = requests.Session()
headers = {"Accept-Encoding":"gzip, deflate","Accept-Language":"en-US,en;q=0.5","User-Agent":"Mozilla/5.0 (Windows NT 6.1; WOW64; rv:26.0) Gecko/20100101 Firefox/26.0","Accept":"text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8","Connection":"keep-alive"}
response = session.get("http://www.example.org/")
The session.get() method would need to be written as:
response = session.get("http://www.example.org/", headers=headers)
Thanks!
I think you are using the first version.
DeleteGet the latest version : https://github.com/h3xstream/http-script-generator
Fix: https://github.com/h3xstream/http-script-generator/issues/2
Doh! Thanks :)
Delete